Quick Starter Controls to Reduce Risks on Industry 4.0 Implementations
The world is getting connected more than ever.
We know that COVID pushed the digital transformation and the cloud solutions, in combination with the broad access of the Internet, turning data consumption economically capable and available, creating an exceptional volume of data nowadays.
According to the website statista.com in 2020, we had a 57% increase in the volume of data generated globally compared to a 24% increase in the previous year. This data increase and technological boost promote the fourth industrial revolution a reality, namely Industry 4.0.
The fourth industrial revolution combines physical elements with emerging technologies such as big data, artificial intelligence, and cloud computing to considerably improve data exchange between business sectors and generate a new concept of “smart manufacturing” that considers continuous production where a flow production method is used to manufacture, produce, or process materials without interruption.
To understand Industry 4.0, we need to learn a bit about each applied technology that compose it and why they are used:
Big Data: As you create a new way to connect the manufacturing environment to produce inter-connected data in real-time, the amount of data produced by these types of equipment is enormous and nonstructured.
Artificial intelligence (AI): The purpose of AI in this environment is to transform data into information. In other words, to give this data meaning for the business. Without AI, this work is pretty much impossible for a human being to analyze this massive amount of data.
Cloud computing: One of the core characteristics of cloud computing is scalability. This feature allows cloud computing to scale up and down according to Big data and AI processing requests. The cloud computing component enables industry 4.0 to fit the purpose of use when dealing economically and technically every time it is needed to handle the amount of data and massive processing information generated by the other technologies.
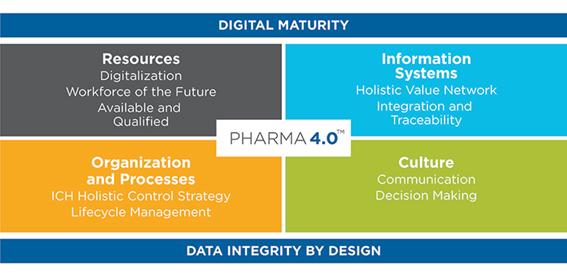
The Pharma 4.0
The pharma industry is not out of this revolution, and ISPE calls the derivative of this concept “Pharma 4.0”. There are already cases of success in using these technologies in the production lines to discover new drugs, reduce maintenance on laboratory or industrial equipment, or develop new ways to maximize the manufacturing processes. It uses all the power of AI/ML, Industrial IoT, and Big Data to transform data into actionable information to revolutionize industrial routines and future operations.
Find below a public illustration of the Pharma 4.0 diagram:
Image Source: ISPE – International Society for Pharmaceutical Engineering
From the moment there is a need to integrate several corporate areas with different new technologies, and it brings the following question:
How to protect the environment from internal and external threats and still meet regulatory requirements, maintaining the integrity and privacy of cGxP data without impacting production?
Firstly, we must consider the challenges and impacts that this enormous amount of data brings to the regulated environment under data privacy (GDPR) and Electronic Records (EudraLex Annex 11 and FDA 21 CFR part 11). Especially with the new technological capabilities that become much more complex in validating computerized systems.
Checking the data reported by Forbes magazine, the Pharma and Healthcare industry has become the 5th largest cyberattack target globally. Based on this, we should pay special attention to the topic of this increasingly connected world.
One avenue to create a secure environment is to look at the ISO 27002 security framework. It describes the controls in the three pillars of People, Processes, and Technology. With the advent of the Internet of Everything, we can adapt it to People, Processes, Data, and Things. The “Internet of Everything” is recognized as a Cisco invention, which builds on the foundation of the “Internet of Things”.
In the people’s subject, training is the keyword. However, in the globalized and interconnected world, it is a complete misunderstanding that information security is just the work of technology teams. Cyberattacks are increasingly sophisticated and focused on exploiting loopholes created by the lack of attention of internal employees, using techniques such as phishing, social engineering, and malicious file propagation.
In the process domain, the computerized system validation process and information security policies such as access control, backup and restore, password management, and especially patching management are the key factors to be considered during the implementation of emerging technologies on pharma 4.0. Most of the vulnerabilities exploited by criminals are due to a lack of hardening of systems (where only approved configuration is enabled) which do not require significant effort and can cause great damage if not applied. In addition, the productive environment of the pharma industry generally uses operating systems that are no longer supported by the supplier but cannot be changed because it might stop the production process.
A solid and elucidative risk assessment (well known risk-based approach) to point out the threats and required controls are extremely necessary, where the goal is to promote cybersecurity and comply with the regulatory requirements (e.g.: encryption during data in transit and at rest, access control extended to interface connections, data location, data processing, and more).
It would be impossible not to mention the ALCOA+ framework when talking about the data. It expects to be Attributable, Legible, Contemporaneous, Original, Accurate, Complete, Consistent, Enduring, and Available. Following this principle, we can maintain the integrity of the data. But where to protect the data in this new environment?
At this point, the concept of Data Integrity by Design emerges. Rather than thinking about protecting the data only when we already have our systems in operation, a new layer of control should be created to discuss how to keep the data safe in the application development phase.
We have a series of Data Integrity blog you can refer to.
In the context of things, we will deal with corporate processes in alignment with emerging technologies. Physical devices and objects should be connected to the Internet and to each other to generate decisions that bring value to the company. It is only going to happen if company internal areas are fully aligned to achieve a common goal.
Conclusion
The job to implement all the controls needed to protect this environment is enormous and varies case by case, and we put together the most important ones with a high impact resulting in reducing the risks involved with Pharma 4.0 technologies and process:
1. Adoption of structured patch management for IT & OT equipment divided into two phases. The first is for new equipment and technology to be implemented with security by design controls, where all critical aspects are treated before it goes live. The second phase is to define how to treat legacy equipment, where they should be separated into three risk levels: Low, Medium, and High based on their impact on the business. With Artificial intelligence, it is possible to check the manufacturing low utilization periods and see the best time to have their maintenance window, offering fewer downtimes for each type of criticality.
2. Implementation of a vast awareness training program for users and people with access to Pharma 4.0 information, mainly for those who have access to change data. If they do not know what kind of cyber threats they are facing, they will not know how to protect themselves.
3. Mapping of equipment and connections between the OT and IT network. With this picture of the environment, it is easy to understand what kind of access people need for each type of technology and check those connections that are not essential for the business and should be blocked to avoid exploiting vulnerable services. In industry 4.0 the machine-to-machine connection is also expected and it should be part of the connection mapping for further risk assessment and security control assurance.
4. A solid Access Control implementation. In combination with item 3, the access control is one of the core controls needed to distinguish the least privilege needed to the data and prevents unauthorized access and violations, not to mention unapproved deletions. Again, it can be used by people or between the equipment and requires good documentation to avoid breaches.
5. IT/OT Governance. Last but not least, the governance aspect must be created and adopted to maintain in a proper manner the implemented controls and further measures to achieve the industrial 4.0 outcomes: real-time data from all parts of the manufacturing process so decisions can be made quickly and efficiently; and automate and streamline processes, reducing waste and increasing productivity and Overall Equipment Effectiveness (OEE).
If you need assistance to understand how to validate your technological environment in this new industrial age and meet internal and external regulatory demands, please contact us.
We will be happy to help you out!